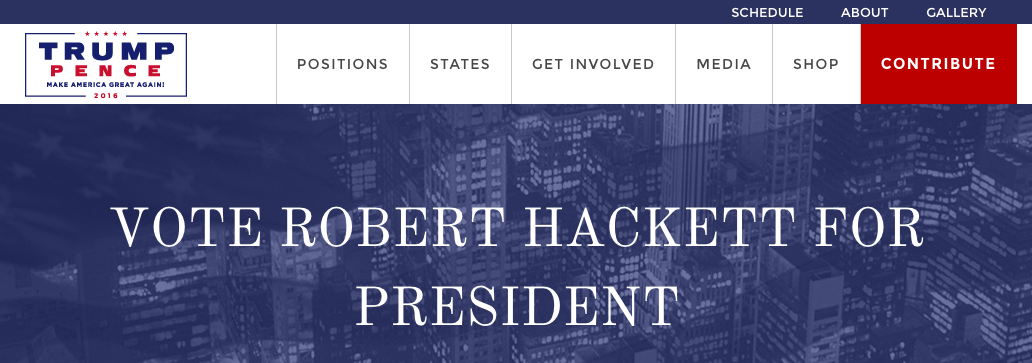
Until recently, Republican presidential candidate Donald Trump’s official campaign website featured an amusing glitch that allowed Internet users to modify its headline text however they so pleased.
The campaign website’s home page auto-generated a default message that encouraged visitors to vote for the Trump ticket. But by editing the text in the page’s URL—replacing words between its “%20” notation dividers, typical URL encoding that denotes spacing—anyone could replace those words with their own message.
Fortune was able to manipulate the entry field before Trump’s team fixed the glitch at about 6 p.m. ET, as seen in the screenshot below. (We do not actually recommend that you vote for the author of this post for president.)
Get Data Sheet, Fortune’s technology newsletter.
Other people had some fun vandalizing the web header as well.
https://t.co/iKQ9riCu3B pic.twitter.com/joq5dAFJf7
— Parker Higgins (@xor) November 8, 2016
https://twitter.com/senatorshoshana/status/796117380111990784
You too can put a random headline on the press releases of Trump's official website. https://t.co/pPtLIKIk7h (h/t @csoghoian) pic.twitter.com/HPhhmakCFI
— Lorenzo Franceschi-Bicchierai (@lorenzofb) November 8, 2016
https://twitter.com/csoghoian/status/796121249143521281
The internet just had a ridiculously fun time with this url hack of Trump’s website https://t.co/mmvVXSOK80 pic.twitter.com/6dv6F8HgnG
— Kashmir Hill (@kashhill) November 8, 2016
Slate originally wrote that someone had “hacked” the website to display a poop emoji. The online publication issued a correction noting that this URL-meddling is not a proper hack, and is only visible on the computer of the person who tampered with the web address.
For more on Donald Trump, watch:
The trick is called “content spoofing,” and it affects about a quarter of all websites, as Jeremiah Grossman, chief security strategist at SentinelOne, an antivirus startup, pointed out on Twitter.
The vuln in Trump’s website is called Content Spoofing, not XSS, which is identified in ~1/4 of all sites. Slide #9. https://t.co/zwWmt9sKvb
— Jeremiah Grossman (@jeremiahg) November 8, 2016
The Trump campaign’s website administrators initially implemented a quick fix that stopped headline text from appearing on the webpage. At least one person soon found a workaround.
Easy to keep the party going in Chrome: right click, "Inspect", & change the <h1> text in sidebar. pic.twitter.com/2MsZom74GA
— Richard Kain (@RichardKain) November 8, 2016
Soon after, the website administrators changed the page to redirect to donaldjtrump.com, the campaign’s homepage, ending the shenanigans.
Incidentally, this back-and-forth between attackers (the vandals) and defenders (the Trump team) exemplifies the cat and mouse game that is cybersecurity.
For more on the election, stay tuned on Fortune.com.